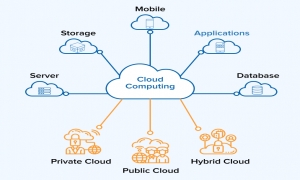
As a rule, attackers try to compromise networks and steal user data, intellectual property, or resources. It doesn't matter whether they are in the public cloud, in the private cloud, or in the physical data center. Based on general experience, Palo Alto Networks offers ten recommendations that help companies ensure that public cloud security is given the same level of attention by protecting their own data centers.
1.Model Provider
Public Security Responsibilities such as Amazon Web Services (AWS) and Microsoft Azure spread "shared responsibility" for security. Operators are responsible for ensuring that the platform is always active, available and up-to-date. Customers are responsible for protecting their own applications and data in the public cloud.
2. Initial Spread Engagement and DevOps Team
Many public cloud projects are being driven by departments such as DevOps, which quickly creates new products or functional prototypes. Ideally, the team and the security department must work together to prevent security risks.
3. Know Your Own Potential Vulnerabilities
Because it's very easy to create a cloud account, the use of public clouds is often referred to as "shadow IT." Employees can unconsciously make security holes. Therefore, it is important to have an overview of who uses public cloud in the company, and it is important to ensure that the environment is properly configured.
4. Understanding
Attackers use automation to find potential targets in minutes. Then they look for security holes or SSH (Secure Shell) that are misconfigured and try a standard password. Understand how attackers' actions are very important to effectively protect applications and data in public clouds.
5. Evaluate
Security Options There are several security options to choose from when you switch to public cloud:
- Cloud providers offer system-owned security services for public clouds such as security groups and WAF (Web Application Firewall). These tools help reduce the surface of the attack, but they themselves contain several security holes. - Host-based security point products are often used to detect and prevent threats. However, IPS (Intrusion Prevention System) only searches for known threats and can ignore zero-day or unknown threats. Like the IDS (Intrusion Detection System), it does not provide a holistic view of the cloud environment.
- Some companies use scripts and transparency tools to protect cloud deployment. A possible disadvantage of the safety strategy of this homemade brand is the lack of management knowledge and lack of support in the event of a security breach.
- Virtualized inline tools, such as virtualized firewalls, provide the basis for understanding all traffic in cloud deployments. Content-based applications, users, and discovery technology help determine who accesses what, and for what purpose. Thus, a dynamic security policy can be applied to protect data and applications in the public cloud from targeted threats and unintentional threats.
6. Knowledge is power
Knowledge in this case ensures that all traffic passes through the mobile, network and cloud environment. By utilizing the next generation of virtualized firewalls as part of an integrated security platform, organizations can gain visibility into the identity and characteristics of traffic to make better decisions about protecting applications and data.
7 Defense is everything.
Some believe that the attacker has "won" and therefore applies the concept of recognition and recovery. With a comprehensive review of the environment, effective defense is indeed possible. Basically, this requires four features: complete transparency, reduced attack surface, defense against known threats, and defense against unknown threats.
8. Cloud-oriented concept
In our own data center, high availability requirements are met by excessive hardware. With a cloud-centric approach, this is easily and quickly achieved through cloud provider structures and related resilience features such as load balancing.
9, Automation to Avoid Congestion
Faster, more accurate security policy updates allow you to operate at cloud speeds. Businesses must look for the following automation tools in their public cloud security mechanisms: non-contact deployment such as bootstrap; two-way integration with third party resources through the API; and policy updates use automation features such as XML API and DAG (Dynamic Address Groups).
10.Policy Consistency
Through Central Management Centralized control of distributed networks with physical and virtual firewalls and the use of a consistent basis of a single security rule from the network to the public cloud is very important. As a result, changing workloads in the public cloud simplifies management and minimizes delays.