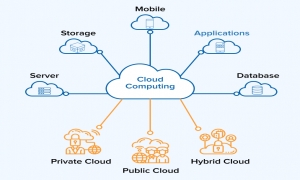
More and more businesses now have a cloud-first strategy. And those who are not ready will immediately define it. Because they all want to benefit from the agility and automation brought by the application in the cloud. However, companies want to focus on the value that applications bring to their business, and not have to worry about uniting individual components. However, large companies that want to push important business applications to the cloud have security issues in the past that have prevented cloud migration. These challenges have been identified and security models have been further developed to remove these obstacles.
This now allows organizations to access advanced security features in the cloud to run highly complex and sensitive workloads in the cloud. For example, the Medicare & Medicaid Service Center operates the Affordable Care Act (ACA) - better known to us as Obamacare, which has allowed more than 24 million Americans to take out health insurance for the first time - fully in the cloud. When such organizations migrate to the cloud with such sensitive data assets, it becomes clear how stringent security requirements must be.
The multi-model database has now been significantly upgraded for comparable applications and offers broad security features. But a very secure database is not enough. Much better cloud security can be provided by so-called data hub services, which use complex security models to raise applications in the cloud to a new level of security.
Three main points for maximum cloud security
1. Virtual Private Cloud.
Unlike other services where many users access a shared infrastructure, the data hub service has each authorized customer in their own virtual private cloud (VPC). With that, each company operates in an environment that is completely different and completely separate from the data, networks, storage and data management of other companies. So, instead of being part of a collection that allocates space for each customer, each participant gets their own Virtual Private Cloud. The Data Hub service using this approach provides the highest level of security: there is no way to turn on or turn off VPC, or even configure it incorrectly. It is precisely this high level of isolation that companies need to protect their data.
2.Advanced encryption.
By default, data in the Data Hub Service must always be encrypted. At the database level, encryption means that even AWS or AzureAdministrator cannot see company data. Even within a company, there are various types and classes of data that can be encrypted differently. This ensures that only authorized people can access the right data at the right time. This encryption represents another level of data separation that businesses need for secure applications in the cloud. With functions such as anonymous level access control and anonymization, data in a data hub is very safe and - in the case of authorized people - can still be highly shared.
3. Maximum security through certification.
Integrated security in the Data Hub thus increases security that has been integrated in the database itself repeatedly. Common-Criteria certification, as provided by SOC 2 Type II principles - security, availability, processing integrity, confidentiality and privacy - is additional evidence that there are adequate policies, procedures and controls for cloud security. They ensure that granular access control, according to company guidelines, can be used only by authorized people in the right context to access data.
The Data Hub Service sets the standard
Businesses rightly expect maximum cloud security. Data Hub Services also bring highly sensitive enterprise applications to the cloud quickly and safely and today sets the security standards companies expect from database technology and cloud services. Certified providers play an important role in all sectors, such as health services, finance, and insurance.
for example, SOC2 Type II certification is a key requirement in the financial industry. Data Hub services can provide a higher level of security than comparable on-premise solutions. The reason for this is application center administration, extended security models and segregation of tasks, made possible by a smooth granular access model. This foundation was created to migrate business critical data to the cloud to be faster and cheaper.